Bootstrapping
The Privakey CX Auth Service must be bootstrapped and configured before it can be used.
Generate Admin Credentials
- From /utils, run
node cred-gen.jsto generate admin credentials. E.G.:
C:\privakeycx\utils> node cred-gen.js
Generating new admin credentials...
Credential generated successfully!
User Name: <generated username>
Password: <generated password>
Use this credential to authenticate to the credential manager.
Note the generated username and password. You will use these to authenticate to the Admin Portal.
Start the ephemeral Admin Server
- From /utils, run
node credential-manager.js. E.G.:
C:\privakeycx\utils> node credential-manager.js
PrivakeyCX Admin server running on localhost:534/
- Open a browser and go to the address displayed on the command line (for the above example, http://localhost:534)
- Use the credentials generated above (in Generate Admin Credentials) to authenticate to the Admin Portal.
Generate Communication Service Credentials
Privakey CX is shipped with a Communication Service that brokers messages from the Auth Service to the Notification Service. If you already have a communication service deployed, instructions on connecting Privakey CX to your communication service can be found here: Sending Notifications
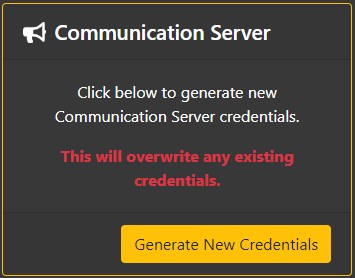
Since the Communication Service is an independent service, you must generate credentials to protect access to it:
- Under the heading Communication Server, click the "Generate New Credentials" button, then confirm by clicking "Generate New Credentials" in the pop-up.
- Set the COMM_SERVER_KEY environment variable to the generated key (See Deployment)
If one ever needs to update the credentials, repeat these steps.
Add your first App Space and Request Origin
App Spaces and Request origins (services that can interact with the Privakey CX server) need to be configured from within the Admin Service. An App Space is defined by the deployment of an App ecosystem with Privakey CX libraries enabled (including a deployment of the Privakey CX White Labeled Applications) and the connection to a singular Authentication Provider.
Creating a New App Space
- In the App Spaces / IDPs section, click "Create New App Space"
- Enter a descriptive name for the App Space in the name field
- Select simple as your Identity Provider Type (If you are using OpenID Connect, see Administration for configuration details)
- Click "Save" and you will be taken to the App Space page
Creating a Request Origin
- Click "View / Manage all Request Origins"
- Click "Create New"
- Enter a descriptive name for the Request Origin in the name field
- Select your Credential Type (HMAC by default)
- Click "Create Request Origin"
- In the Overview section, make note of the User Id, as you will need this to authenticate to the Privakey CX Server
- In the Credential updated section, click the "Show Secret" button and copy the secret, as you will need this to authenticate to the Privakey CX server
Start the server
The server is now configured and ready to be started.
Simply run npm start from project root.
You can test that everything is up and running by performing a GET request at the base URL. E.G. GET http://localhost:8080
Next steps
See how to administer the CX Service here.
View the API documentation here.
Updated over 6 years ago
